Billions at Stake: Unveiling and Mitigating Double-Spending Attacks in Arbitrum’s Rollback Mechanisms
Other Articles

How a Pioneering Security Analysis Exposed Critical Vulnerabilities in Ethereum's Leading Optimistic Rollups and Safeguarded the Future of DeFi
Study conducted by Prof. Daniel Xiapu LUO and his research team

Ethereum's meteoric rise as the backbone of decentralised finance (DeFi) has brought both innovation and new security challenges. As transaction volumes soared, Layer-2 solutions such as optimistic rollups, most notably Arbitrum and Optimism, emerged to address scalability. Yet, the rapid adoption of these protocols has outpaced the scrutiny of their security models, leaving billions of dollars potentially exposed.
In a landmark research effort published in Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security [1], Prof. Daniel Xiapu LUO, Associate Dean (Research) of the Faculty of Computer and Mathematical Sciences and Professor of the Department of Computing at The Hong Kong Polytechnic University, led his research team to identify and uncover critical double-spending vulnerabilities in both Arbitrum and Optimism, earning half a million dollars in bug bounties and prompting urgent protocol upgrades that ultimately protected the assets of countless users and DeFi protocols.
The achievements of this research are both significant and far-reaching. Through meticulous analysis and experimental validation, the research team uncovered three previously unknown double-spending attacks targeting Arbitrum's rollback mechanisms. These attacks, if left unaddressed, could have enabled malicious actors to steal funds from cross-chain applications, undermining the very trust that underpins the DeFi ecosystem. The generalisability of the findings was demonstrated by successfully adapting the attacks to target Optimism.
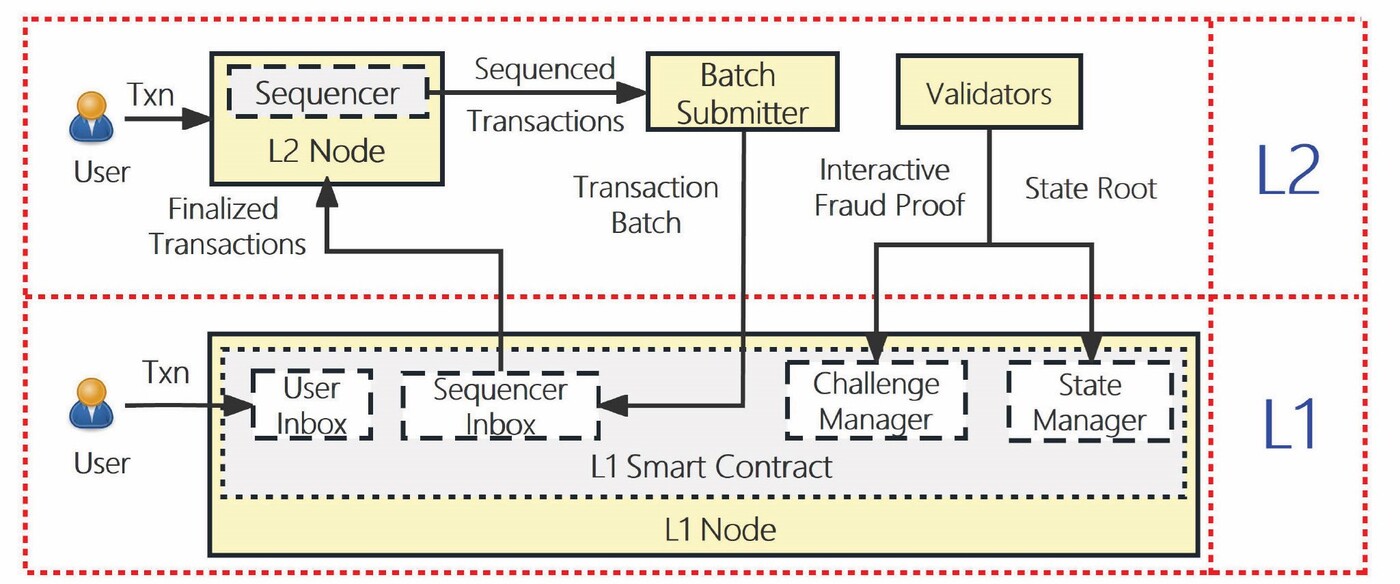
Figure 1. Overview of the optimistic rollup protocol
To appreciate the gravity of these findings, it is essential to understand the technical landscape in which they surfaced. Ethereum's scalability challenges have driven the adoption of Layer-2 protocols, with optimistic rollups emerging as a dominant solution for boosting throughput and reducing costs. In optimistic rollup systems such as Arbitrum and Optimism, the architecture is divided between Layer-2 (L2) and Layer-1 (L1) components (Figure 1). On L2, key roles are played by sequencers, which order and execute user-submitted transactions; batch submitters, which aggregate these transactions into batches; and validators, which periodically compute and submit the state root of the L2 blockchain.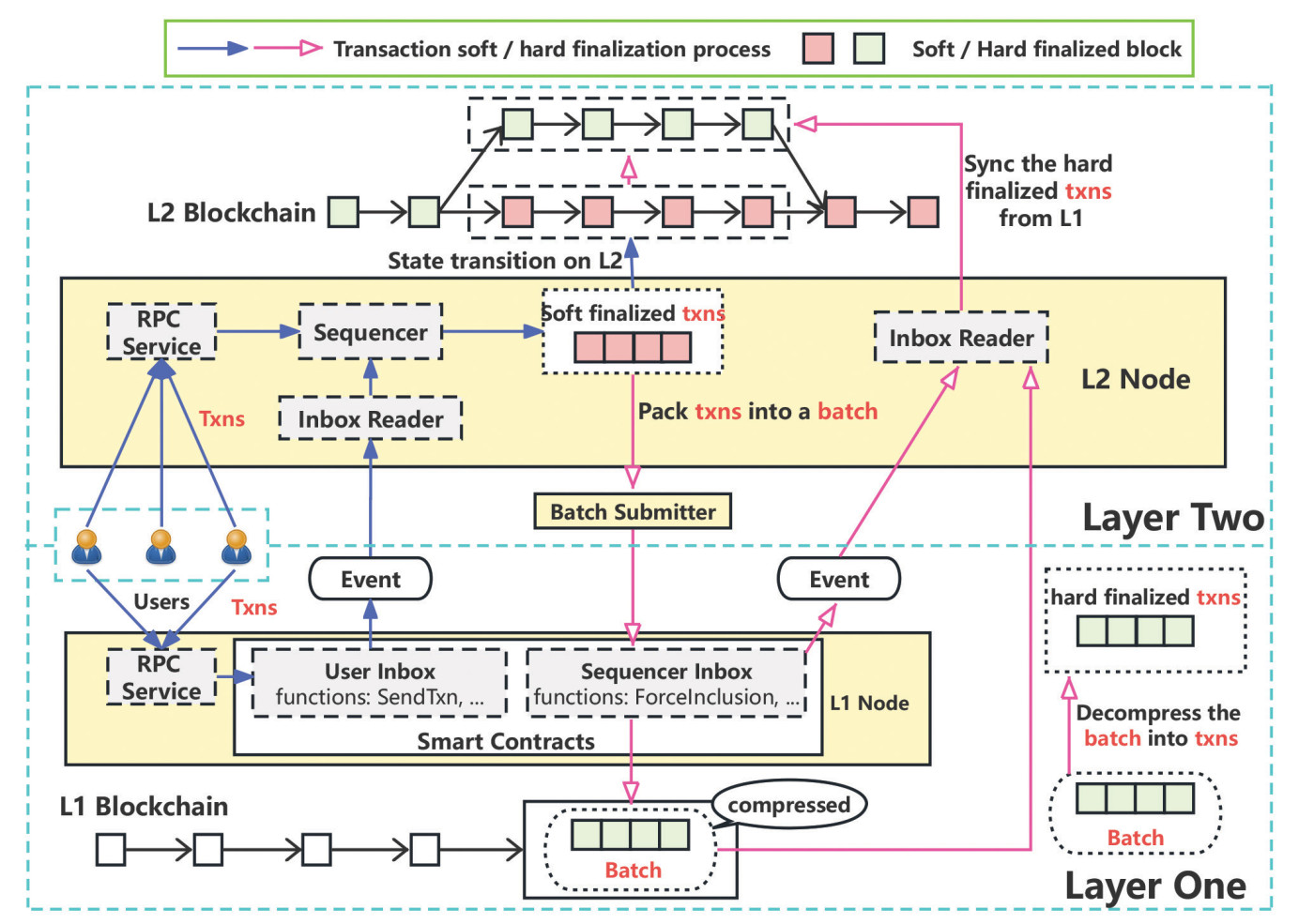
Figure 2. Life cycle of transactions on Arbitrum. The blue arrows illustrate the process of transactions from being accepted to reaching the soft finalised state. The pink arrows show the process from soft finalised to hard finalised state.
The process begins when a user sends a transaction to the L2 node, where it is sequenced and executed, achieving what is known as soft finality (Figure 2). These transactions are then compressed and grouped into batches by the batch submitter. The batches, along with the computed state roots, are periodically posted to L1, where smart contracts on Ethereum's mainnet record the transaction data and state roots, anchoring the security and finality of the system. Validators on L1 can challenge incorrect state roots by submitting fraud proofs within a designated window, ensuring correctness. Once a batch is confirmed on L1, the transactions within it reach hard finality.
However, if discrepancies arise between the soft-finalised and hard-finalised states, such as through L1 reorganisations or protocol-specific mechanisms, the L2 node may roll back soft-finalised transactions to maintain consistency. This co-ordinated flow between L2 and L1 underpins the efficiency and security of modern DeFi, with Arbitrum and Optimism now securing billions in total value locked.
While this dual-finality model enhances efficiency, it also introduces a window of vulnerability. Many cross-chain applications, such as bridges, act on transactions as soon as they achieve soft finality, in the interest of speed and user experience. But if an attacker can force a rollback of these soft-finalised transactions before they are hard-finalised, the door is opened to double-spending attacks, where the same funds are spent twice, potentially across different chains.
Prof. Luo's team systematically dissected Arbitrum's architecture, identifying three core mechanisms that could trigger state rollback:
1. Time Bound Mechanism
To prevent chain reorganisations and timestamp manipulation, Arbitrum enforces a time window (typically 24 hours) within which L2 transactions must be submitted to L1. If a transaction's finalisation is delayed beyond this window, the protocol corrects the timestamp and rolls back the affected soft-finalised transactions.
2. Liveness-Preservation Mechanism
Designed to ensure censorship resistance, this mechanism allows users to force the inclusion of their transactions via L1 if the sequencer becomes unresponsive. However, if a forced inclusion occurs after a delay, it can create inconsistencies between the L1 and L2 transaction queues, triggering a rollback of queued soft-finalised transactions.
3. Transaction (De)compression Mechanism
To reduce costs, Arbitrum compresses batches of transactions before submitting them to L1. However, if a batch decompresses to a size exceeding the protocol limit, the L2 node deems it invalid and rolls back all associated soft-finalised transactions.
Central to the success of the double-spending attacks is the "manipulable delay attack", a technique devised to inject arbitrary delays into the transaction rollup process. By flooding the L2 with large, incompressible transactions, an attacker creates a backlog that prevents timely batch submission to L1. This delay is the linchpin that enables the exploitation of the aforementioned rollback mechanisms. Three double-spending attacks trigger rollbacks in this way.
1. Overtime Attack
By deliberately inducing a backlog, an attacker delays the finalisation of targeted transactions beyond the time bound. When the window is exceeded, the protocol rolls back the soft-finalised transactions (Figure 3). If a cross-chain bridge has already acted on a transaction, such as minting tokens on another chain, the attacker can withdraw the minted assets while also reclaiming their original deposit on Arbitrum, thus achieving a double spend.
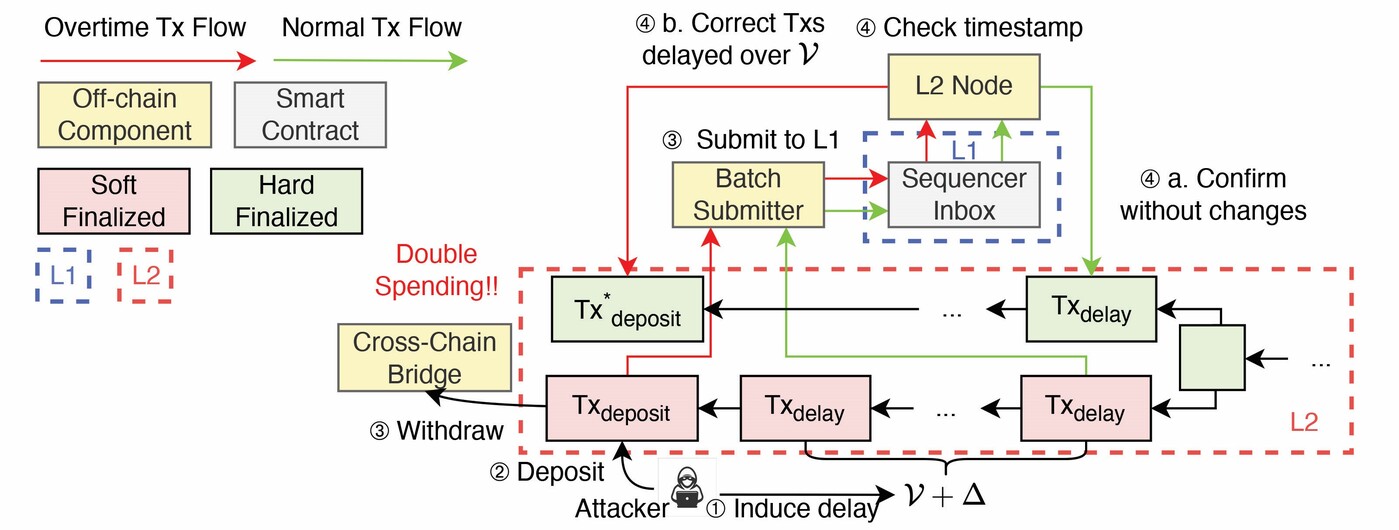
Figure 3. The workflow of overtime attack. Txdeposit is the cross-chain deposit transaction, Txdelay is the delay-inducing transaction, ν is the submission window, and Δ is the timeframe allocated for submitting Txdeposit to L2.
2. QueueCut Attack
The attacker first creates a queue of delayed soft-finalised transactions. Then, by submitting a transaction from L1 and forcing its inclusion at the front of the queue, the attacker causes a misalignment between the soft-finalised and hard-finalised transaction queues (Figure 4). This triggers a rollback of the queued transactions, including any cross-chain deposits the attacker wishes to double spend.
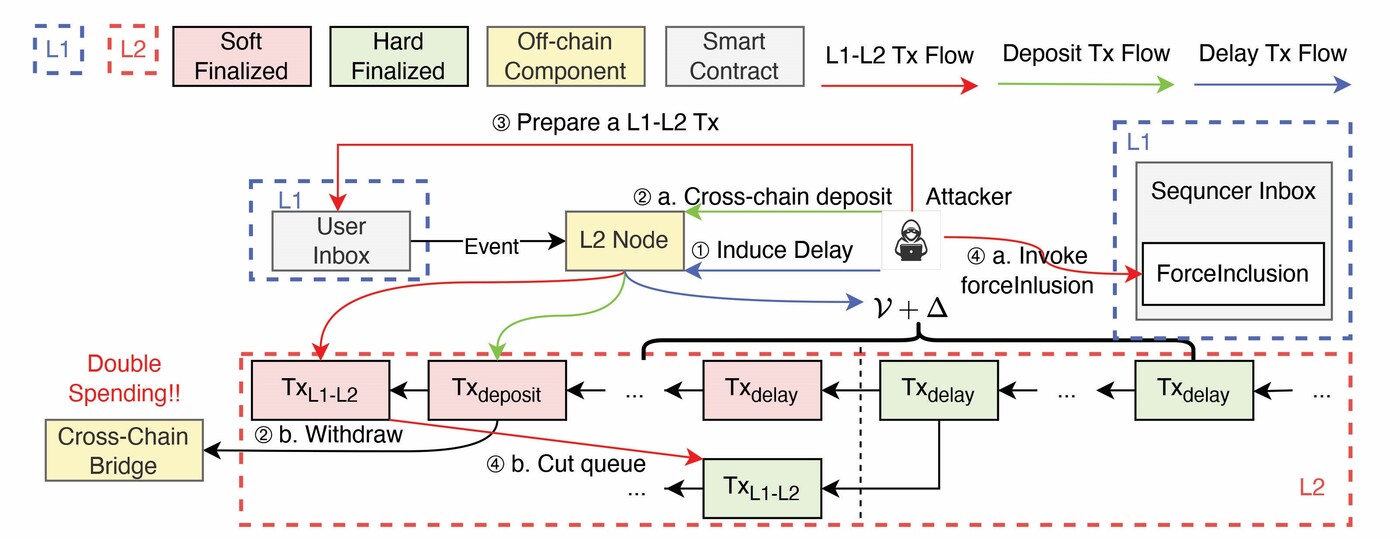
Figure 4. Workflow of QueueCut attack
3. Zip-Bomb Attack
By crafting a batch with highly compressible (e.g., zero-padded) transactions, an attacker creates a batch that, once decompressed, exceeds the permitted size due to a bug in Arbitrum's implementation. This causes the L2 node to deem the batch invalid and roll back all associated soft-finalised transactions (Figure 5), again enabling double spending if cross-chain bridges had already acted on the reverted transactions.
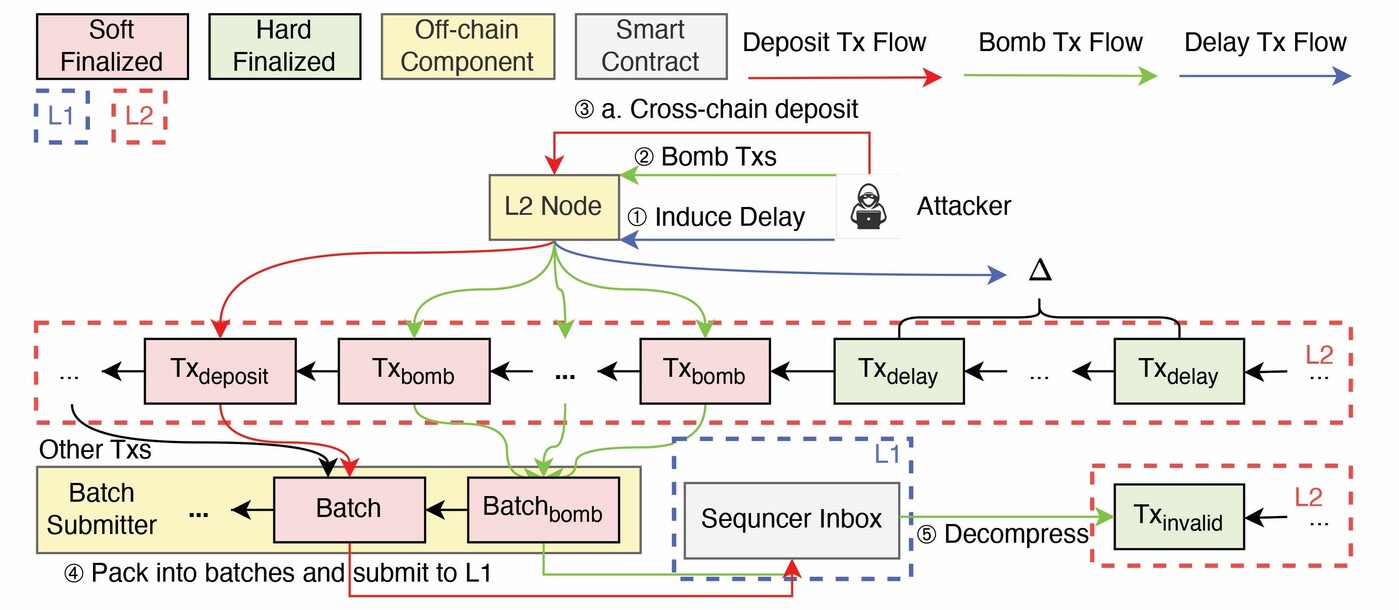
Figure 5. Launch of a double spending attack via zip-bomb
Recognising the potential cost of such an attack, the team also devised a cost optimisation strategy. By manipulating the posting unit price and carefully controlling the transaction submission rate, it demonstrated that the attack could be executed at a reasonable or even constant cost. Notably, they revealed an implementation error in Arbitrum's fee adjustment logic, which could amplify the impact of such attacks, causing transaction fees for all users to skyrocket in the aftermath.
In response to responsible disclosure, both Arbitrum and Optimism undertook significant mitigations.
Arbitrum introduced a new "data poster" component to submit batches to L1 in a streaming fashion, eliminating the batch backlog issue and closing the window for delay-based attacks. Further, a hard fork (ArbOS version 10) introduced safeguards against manipulation of the posting unit price and the batch submitter was updated to track plaintext transaction sizes, preventing zip-bomb exploits.
Optimism, in its Bedrock hard fork, overhauled its transaction pool and batch submission logic, introducing priority fees, fixed block intervals and parallel batch posting to L1. These changes collectively neutralised the identified attack vectors, restoring confidence in the security of optimistic rollups. Additionally, cross-chain bridge projects were urged to await L1 inclusion before acting on transactions, further reducing systemic risk.
Besides this research on the security of optimistic rollups, Prof. Luo and his team also uncovered severe vulnerabilities in zero-knowledge rollups [2,3], another major layer-2 solution for scaling blockchain. Furthermore, they identified denial-of-service issues affecting both types of rollups [4]. Their ongoing research continues to push the boundaries of blockchain security and performance. Notably, Prof. Luo's latest work explores the acceleration of smart contract fuzzing using GPUs [5]. By transforming EVM bytecode and fuzzing logic into parallel GPU tasks, his prototype achieves up to 15.38 times higher throughput than existing tools, enabling the detection of more bugs and greater code coverage—an essential step towards more robust smart contract ecosystems.
Prof. Luo has been recognised by Stanford University as one of the top 2% most-cited scientists worldwide (career-long) in the field of information and communication technology in 2025, and one of the top 2% most-cited scientists worldwide (single-year) for six consecutive years, from 2020 to 2025. He was elected a Distinguished Member of Association for Computing Machinery (ACM) for his outstanding contributions to safeguarding blockchain, smart contracts, Android and its applications in 2024. He also received the Bank of China (Hong Kong) Limited Science and Technology Innovation Prize (FinTech) 2023 for his contribution to blockchain security. His research has led to more than 10 best/distinguished paper awards at top conferences and several awards from the industry. This research paper, in particular, received the Distinguished Paper Award from the ACM Conference on Computer and Communications Security 2024 and the Best Practical Paper on Cybersecurity Award 2025.
| References |
|---|
[1] Sun, Z., Li, Z., Peng, X., Luo, X., Jiang, M., Zhou, H., & Zhang, Y. (2024). DoubleUp Roll: Double-spending in Arbitrum by Rolling It Back. Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security (CCS '24). Association for Computing Machinery, New York, NY, USA, 2577–2590. https://doi.org/10.1145/3658644.3690256.
[2] Li, Z., Peng, X., He, Z., Luo, X. & Chen, T. (2024). fAmulet: Finding Finalization Failure Bugs in Polygon zkRollup, Proceedings of the 2024 ACM Conference on Computer and Communications Security (CCS’24). Association for Computing Machinery, New York, NY, USA, 971–985. https://doi.org/10.1145/3658644.3690243.
[3] Peng, X., Sun, Z., Zhao, K., Ma, Z., Li, Z., Jiang, J., Luo, X. & Zhang, Y. (2025). Automated Soundness and Completeness Vetting of Polygon zkEVM, Proceedings of the 34th USENIX Security Symposium (USENIX SEC), Seattle, USA, August 2025. https://www.usenix.org/conference/usenixsecurity25/presentation/peng-xinghao.
[4] Li, Z., Sun, Z., He, Z., Chu, J., Zhou, H., Luo, X., Chen, T. & Zhang, Y. (2025). Denial of Sequencing Attacks in Ethereum Layer 2 Rollups. Proceedings of the 2025 ACM Conference on Computer and Communications Security (CCS’25). Association for Computing Machinery, New York, NY, USA, 2025.
[5] Chen, W., Luo, X., Cai H., & Wang, H. (2024). Towards Smart Contract Fuzzing on GPUs, 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 2024, pp. 2255-2272, doi: 10.1109/SP54263.2024.00229.
 | Prof. Daniel Xiapu LUO |



